Burlington Telecom Internet Customers | Get flightmobile for only $10 a month for one year!* Join the VIP List!
Burlington Telecom Internet Customers | Get flightmobile for only $10 a month for one year!* Join the VIP List!
The evil hackers of the world are at it again. This time, phishers are sending fake emails to Office 365 users via malicious links inserted into SharePoint documents. This latest trick allows phishers to bypass the platform’s built-in security. The campaign, dubbed “PhishPoint,” is spread to victims via emails containing a SharePoint document and invitation to collaborate. However, when clicked, the file contains a nasty URL that snatches end users’ credentials. The phishing attack has hit some 10% of Office 365 customers globally.
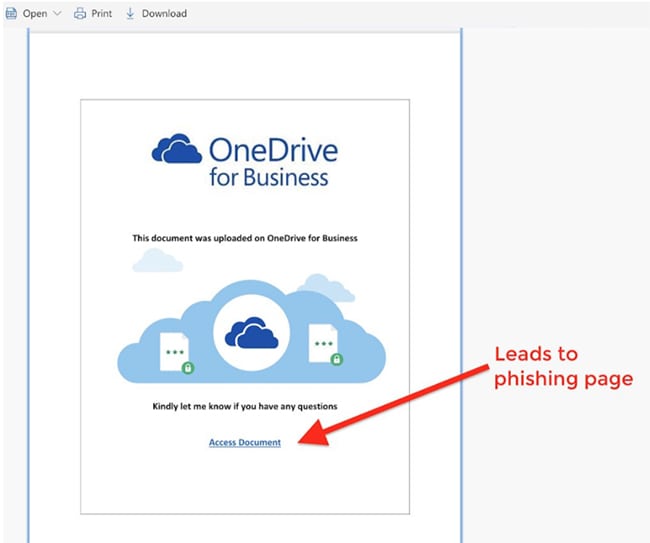
The victim receives an email containing a link to a SharePoint document. The body of the message is identical to a standard SharePoint invitation to collaborate. After clicking the hyperlink in the email, the victim’s browser automatically opens a SharePoint file. The SharePoint file content impersonates a standard access request to a OneDrive file, with an ‘Access Document’ hyperlink that is actually a malicious URL.
Office 365 has multiple layers of defenses that detect this type of attack. Users are still encouraged to check the authenticity of the links prior to clicking them, avoid opening links in emails from senders they don’t recognize, or visiting unsecured sites. Basic good practices include being aware of any email subject line that capitalizes buzzwords (like “Urgent” or “Action Required”) and staying suspicious of any URLs that show up in the body of emails.